Discord Nitro RANSOMWARE
Discord Nitro gift code now demanded as RANSOMWARE payments !!!
A new ransomware calling itself 'NitroRansomware' encrypts victim's files and then demands a Discord Nitro gift code to decrypt files.
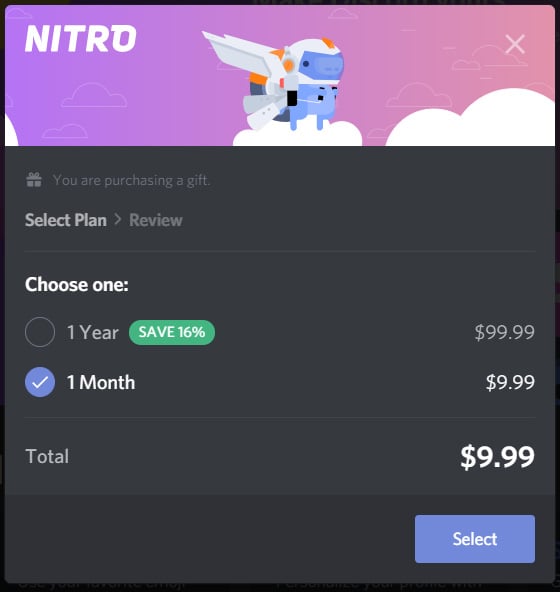
While Discord is free, they offer a Nitro subscription add-on for $9.99 per month that provides additional perks, such as larger uploads, HD video streaming, enhanced emojis, and the ability to boost your favorite server, so its users enjoy extra functionality as well.
Not your typical ransom demand
While most ransomware operations demand thousands, if not millions, of dollars in cryptocurrency, Nitro Ransomware deviates from the norm by demanding a $9.99 Nitro Gift code instead.
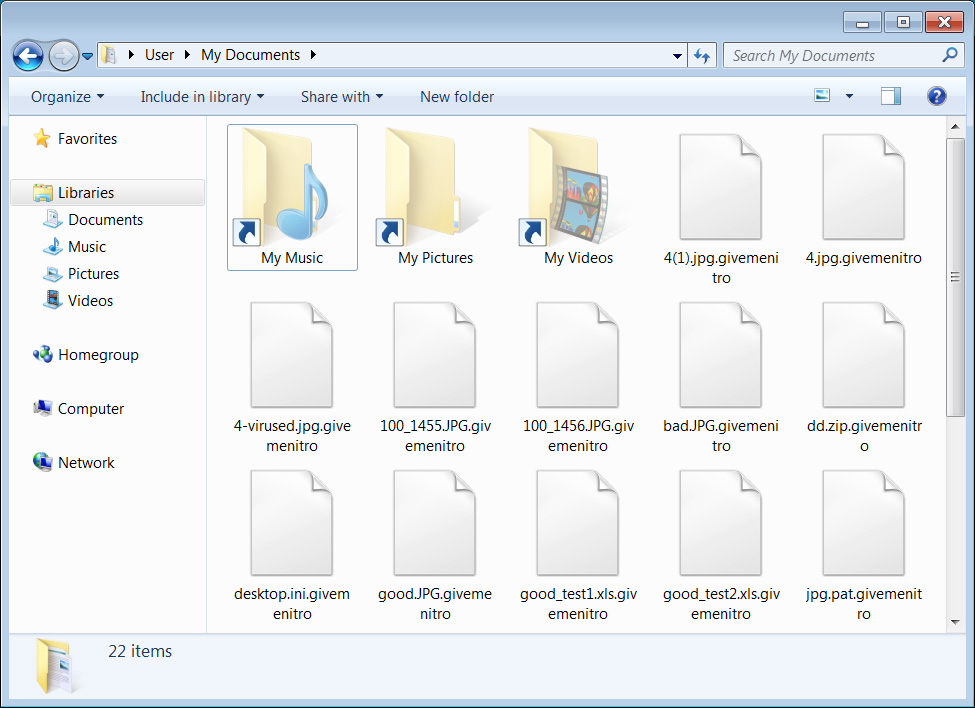
Based on filenames for NitroRansomware samples this new ransomware appears to be distributed as a fake tool stating it can generate free Nitro gift codes.
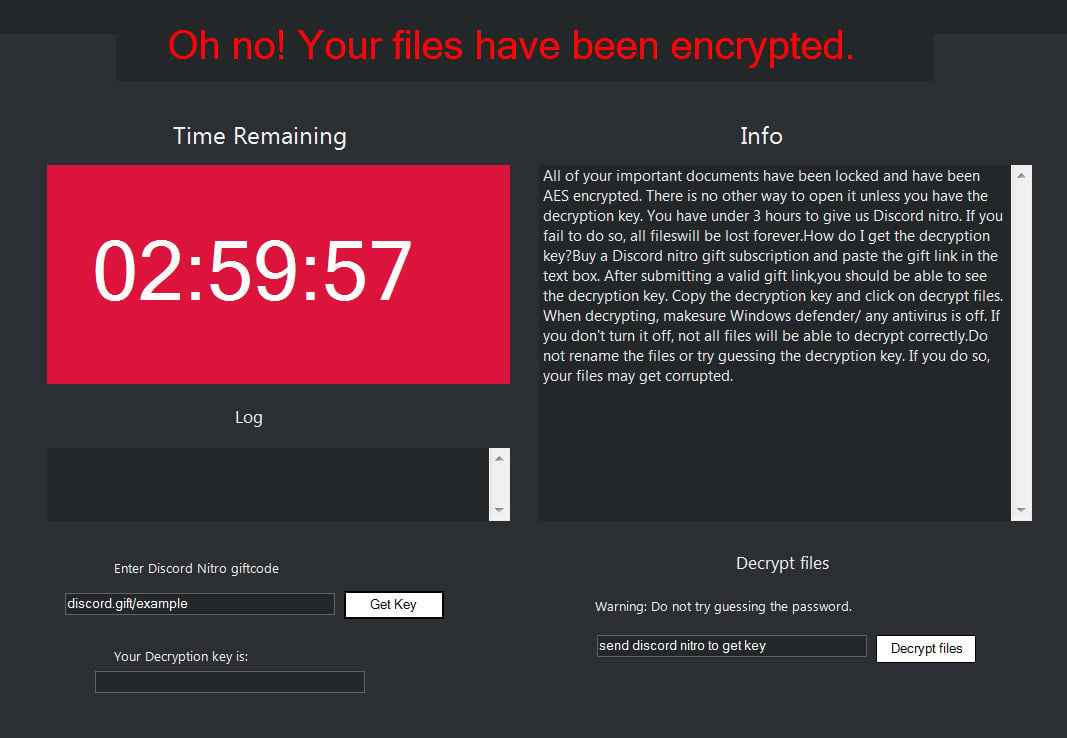
The ransomware disguises as a fake tool that generates Nitro gift codes for free, which will then encrypt the victim’s files once executed. NitroRansomware changes the user’s wallpaper into an angry or evil Discord logo after the execution is completed. After the wallpaper is changed, a ransomware screen appears, which demands a free Nitro gift code within a three-hour period; otherwise, the victim’s encrypted files will be deleted. However, there is no evidence showing that any user files has been deleted if the victim fails to pay on time.
Files encrypted by the NitroRansomware
Aside from demanding gift codes and encrypting victims’ files, the ransomware also steals the person’s Discord tokens, which when stolen, could be used by the hacker to log in as that user. The malware will also try to steal information Google Chrome, Yandex Browser and Brave Browser.
Discord tokens are authentication keys tied to a particular user, that when stolen, allow a threat actor to log in as the associated user.
When NitroRansomware starts, it will search for a victim's Discord installation path and then extract user tokens from the *.ldb files located under "Local Storage\leveldb." These tokens are then sent back to the threat actor over a Discord webhook.
The good news is that this ransomware does not do a good job hiding its decryption key, and users can recover their files for free.
However, the bad news is that the threat actor will likely have already stolen a user's Discord token.
Due to this, users infected with this ransomware should immediately change their Discord password in case their account has been compromised.



Comments
Post a Comment